RED INTO GREEN
Personal data protection management system
An app which helps you tidy up, automate and support processes related to personal data protection (GDPR).
RED INTO GREEN features a range of functionalities which streamline your work so that you can effectively support organizations through reports and records.
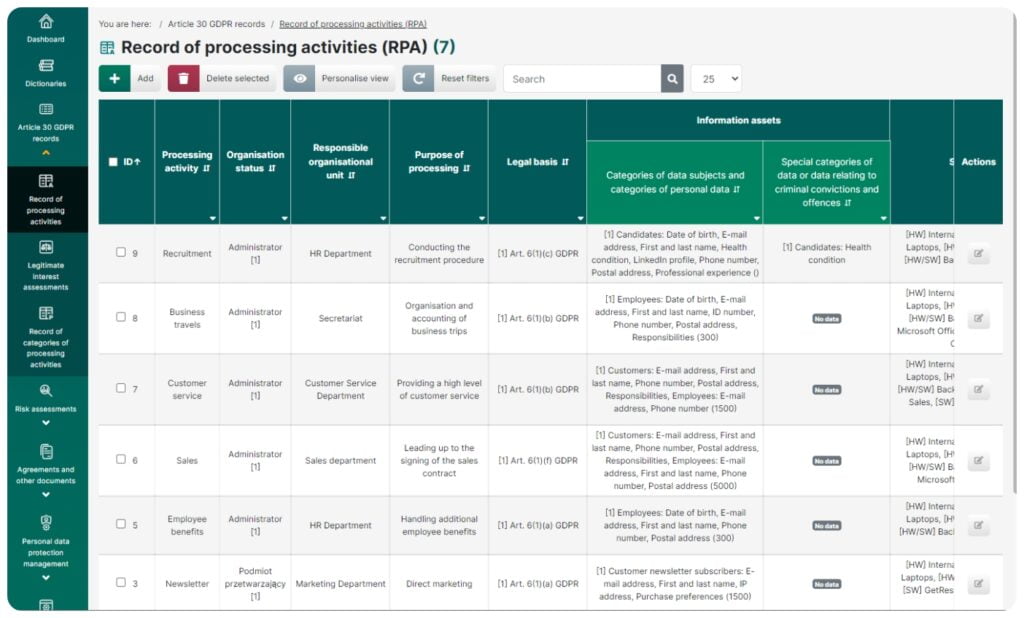
Record of processing activities
This feature lets you create a record of activities:
- Fully compliant with the regulations and recommendations of the Personal Data Protection Office
- Based on dictionaries used simultaneously in many places across the app which enables standardization of records and accelerates work
- Allowing to demonstrate which resources in an organization are used during particular processing activities
- Including a system which automatically displays technical and organizational security measures by linking them to the assets
- Including a system which automatically displays details such as processors, categories of recipients, third countries, safeguards for data transfers outside the EEA – all based on their links created in the dictionaries
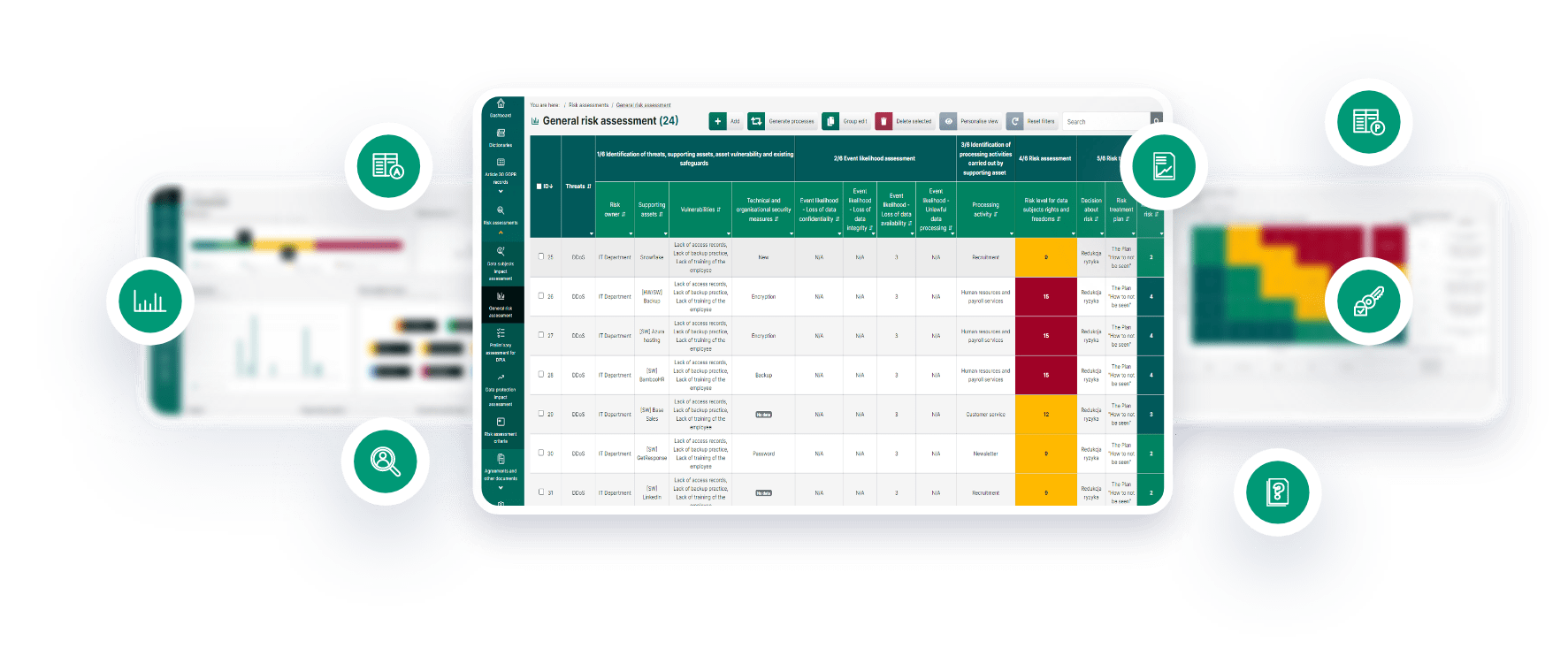
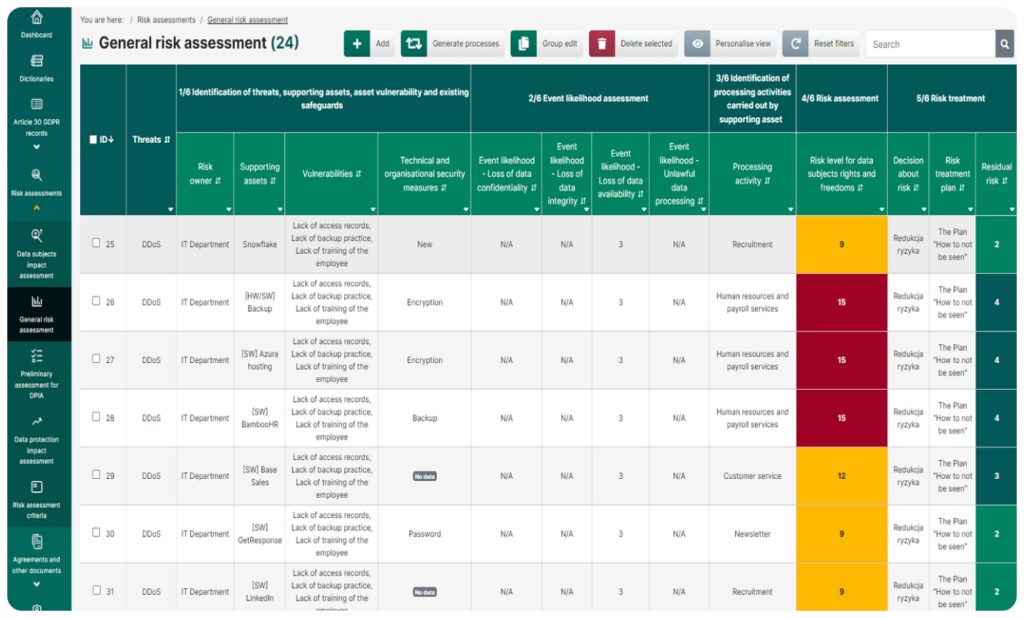
General risk assessment
This module helps you meet the requirements of Articles 24 and 32 of the GDPR. This feature of the system is as automated as possible, and lets you create a list of all the processing activities (along with threats) through the supporting assets (resources) used. Having the data shown in a table will enable you to:
- Identify the resource owners and risk owners; determine the susceptibility of recources which may contribute to creating threats; indicate these resources’ safeguards which can prevent these threats
- Evaluate the likelihood that a threat can become real and the data can lose a specific security attribute (confidentiality, integrity, availability, lawfulness)
- Assess the value of risk based on an evaluation of the likelihood and severity of impact for data subjects for each processing activity in a separate dashboard
- Develop a detailed risk management plan for specific threats, assets or activities, including assigning one plan to many combinations
- Predict the impact of the risk management plan on the value of the risk from the initial evaluation
- Check whether it is necessary to carry out a data impact assessment based on the risk assessment results. Thanks to the group editing feature, each of the above operations can be carried out simultaneously for up to several hundred records
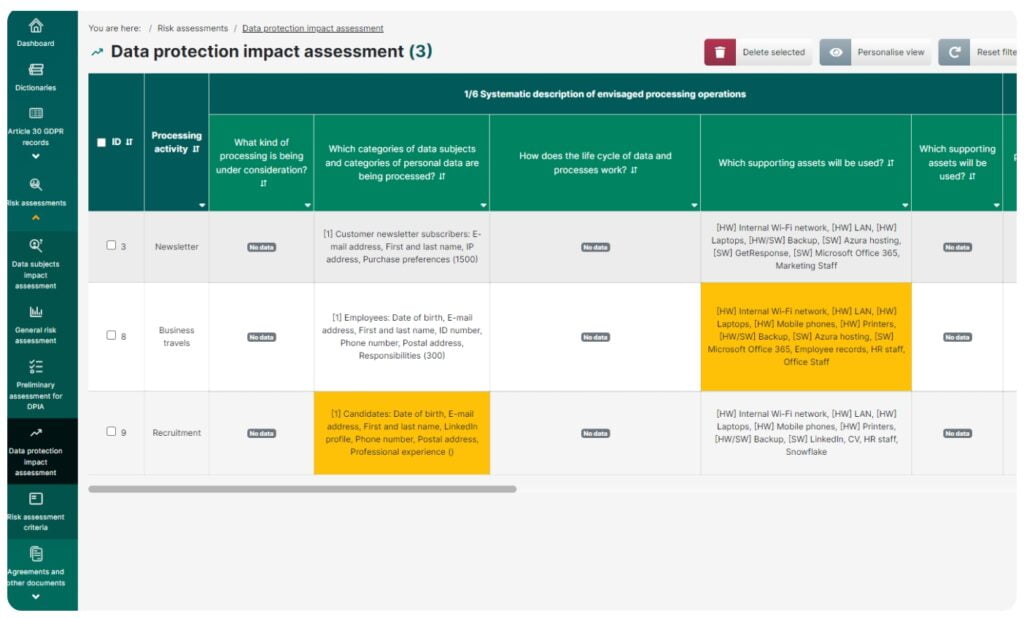
Data protection impact assessment (DPIA)
This feature lets you carry out a full data protection impact assessment by:
- Evaluating whether it is required to carry out a data protection impact assessment
- Assessing how likely it is that a high risk occurs of infringement of the rights and freedoms of natural persons
- Collecting all the necessary information needed to carry out the assessment:
- Description of planned processing activities
- Evaluation of proportionality and necessity
- Assessment of the risk of infringement of the rights and freedoms (in the General risk assessment module)
- Description of envisaged risk-mitigating measures
- Documentation of any consultations held, including with the supervisory authority
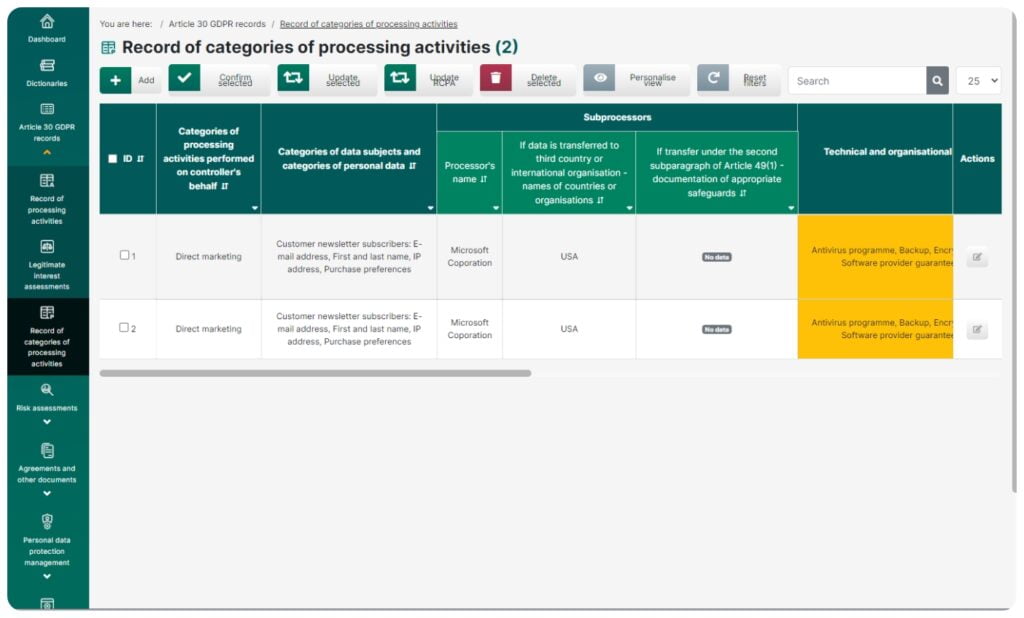
Register of the categories of processing
This feature lets you create a fully compliant record of the categories of processing activities in which the organization shows a list of activities performed for other entities. The module allows you to define categories and copy them for many controllers (if the same range of services is offered to many organizations).
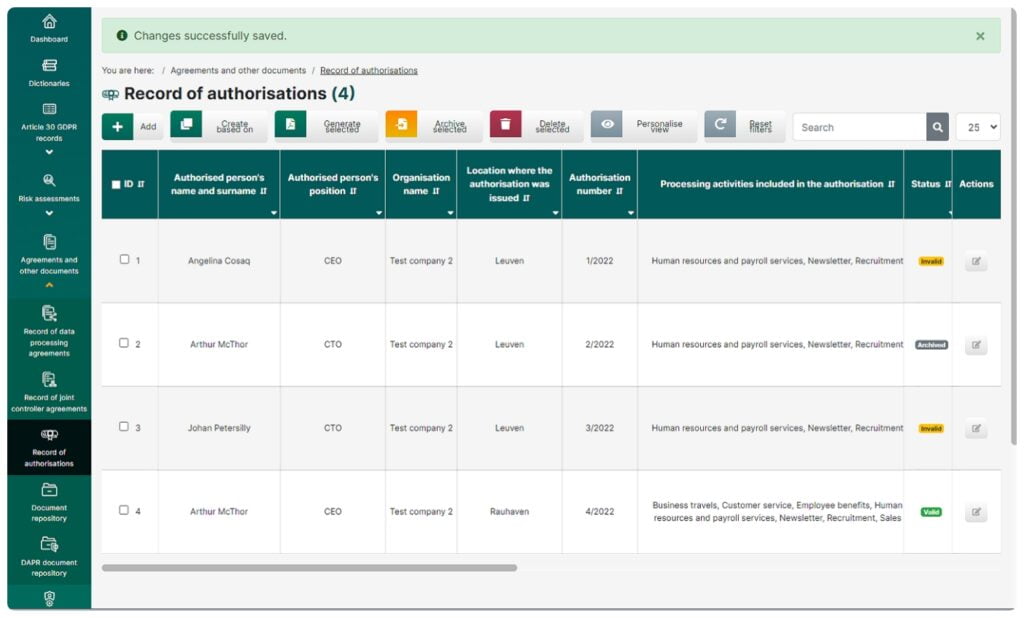
Record of authorizations
This feature lets you quickly generate ready-to-print authorization documents for personal data processing.
- The module makes use of the links which exist among the authorizations, the processing activities and the range of data that are processed.
- It uses flexible solutions enabling you to create new authorizations based on previously defined models.
- You will always know if your authorizations are up to date thanks to the link between the record of processing activities and the system of statuses.
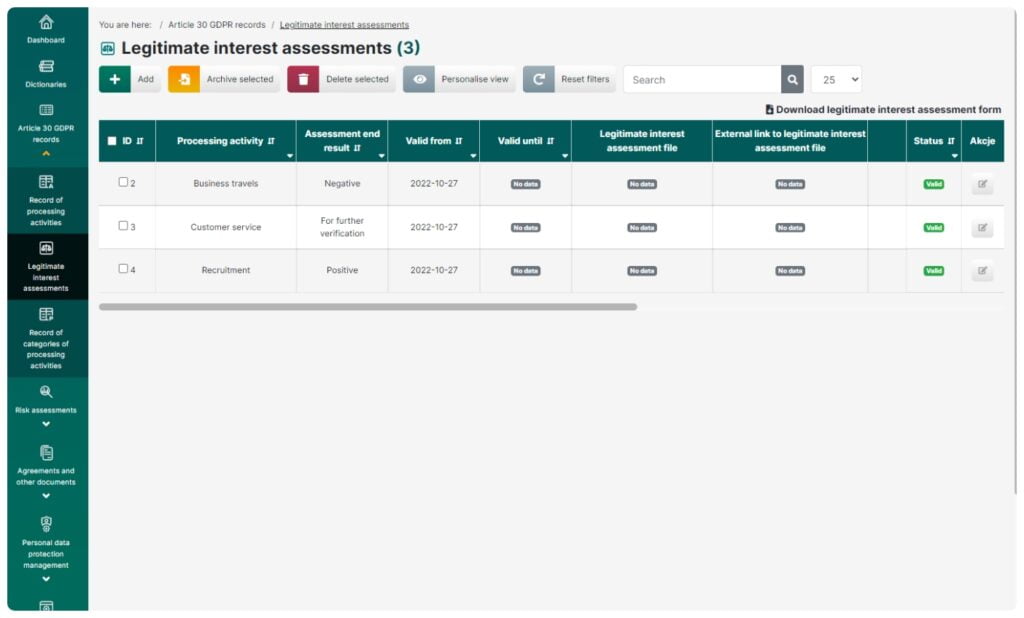
Legitimate interest assessment
This feature can be used to evaluate and prove whether a legitimate interest of a controller or a third party can provide the legal grounds for a particular processing activity (Article 6(1)(f) of the GDPR). According to the guidelines, the assessment includes:
- Test of Interest
- Test of Necessity
- Test of Balance
- Full asssessment report
Record of data processing agreements /
Record of joint controller agreements
These features allow you to:
- Keep a record of data processing agreements
- Verify processors
- Store copies, scans and drafts of agreements
- Save, archive and manage agreements between joint controllers
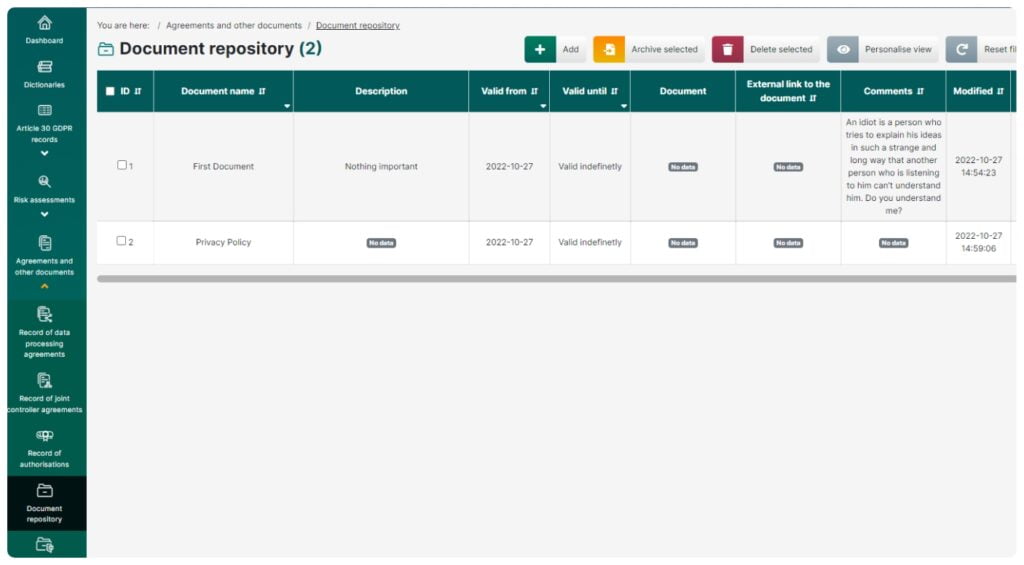
Repository of documents /
Repository of DAPR documents
These features enable you to:
- Store and keep a record of policies, procedures, templates and any other company documents related to personal data protection
- Use document templates prepared by DAPR

Record of incidents and breaches
This feature allows you to:
- Evaluate an event and qualify it as a security incident or a personal data breach
- Assess the risk following a personal data breach and identify a recommended procedure for notifying the supervisory authority, the controller and the data subjects
- Assess the risk of a breach using two methods: ENISA and DAPR
- Automatically prepare a notification for the supervisory authority, a message for the data controller and the data subjects using the DAPR assessment form
- Keep a record of security incidents and personal data breaches
- Store documentation related to an incident/breach
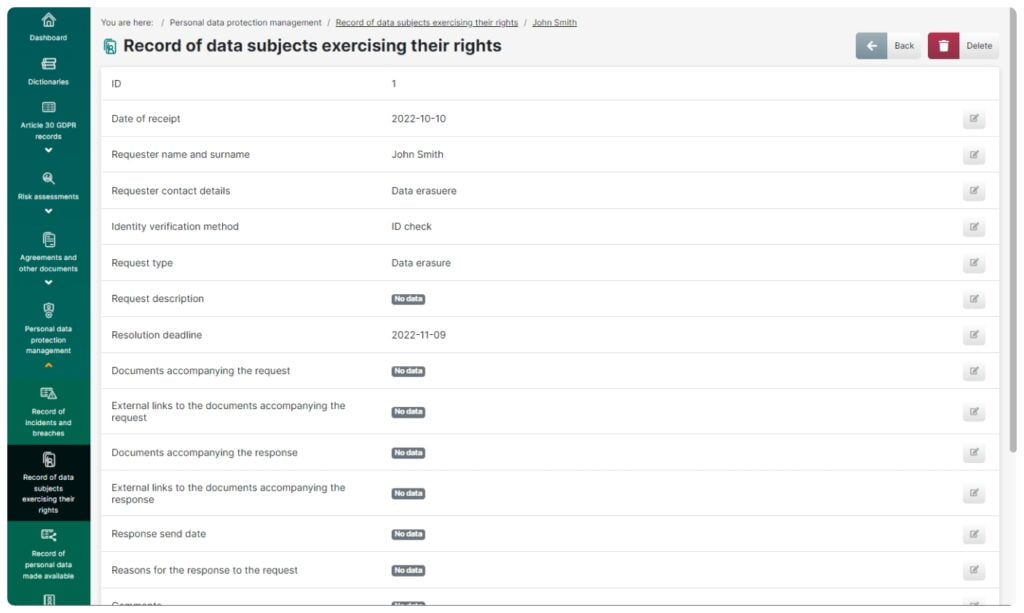
Record of data subjects exercising their rights
This feature enables you to:
- Keep a record of and categorize requests of data subjects
- Keep an eye on timely completion of requests: once a new request is added, a relevant deadline is applied
- Make a comparison of individual requests
- Store documents related to requests, such as scans, responses and other items
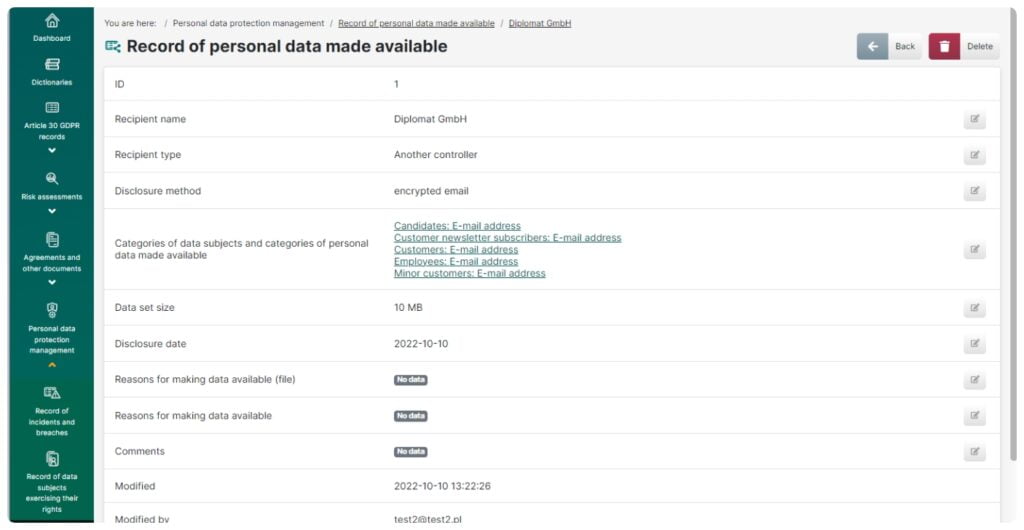
Record of making personal data available
This feature allows you to:
- Keep a record of all the occasions when personal data have been made available by the organization
- Categorize recipient types and to keep a record of the types and sizes of files which have been made available
- Store documents which specify the grounds for making the files available, such as requests and agreements
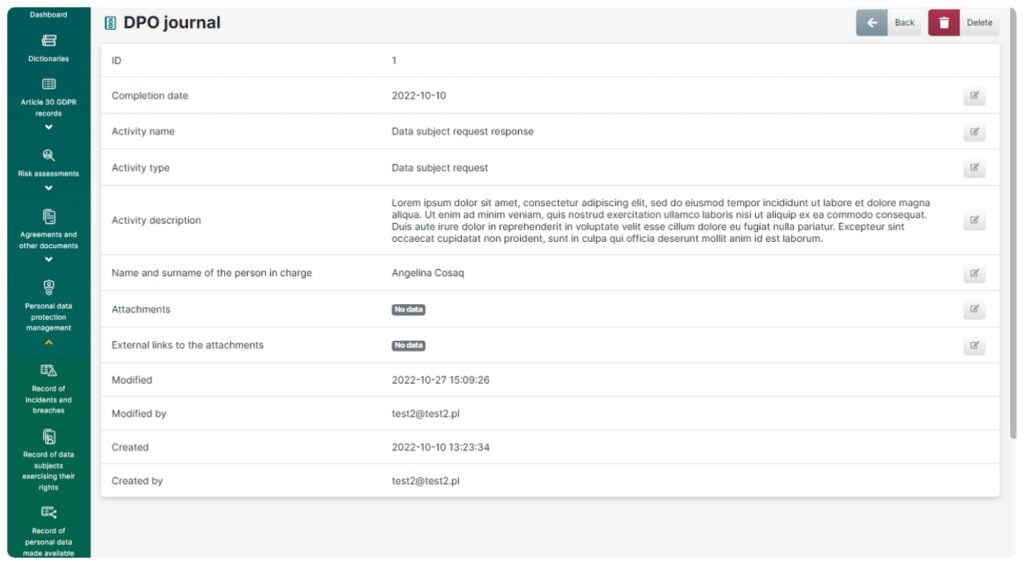
DPO Journal
This feature enables you to:
- Keep a detailed record of DPO’s operations to ensure accountability
- Store documents which confirm that activities have been performed
- Plan DPO’s activity
- Collect information on training courses, audits and recommendations, which can be stored as part of the documentation
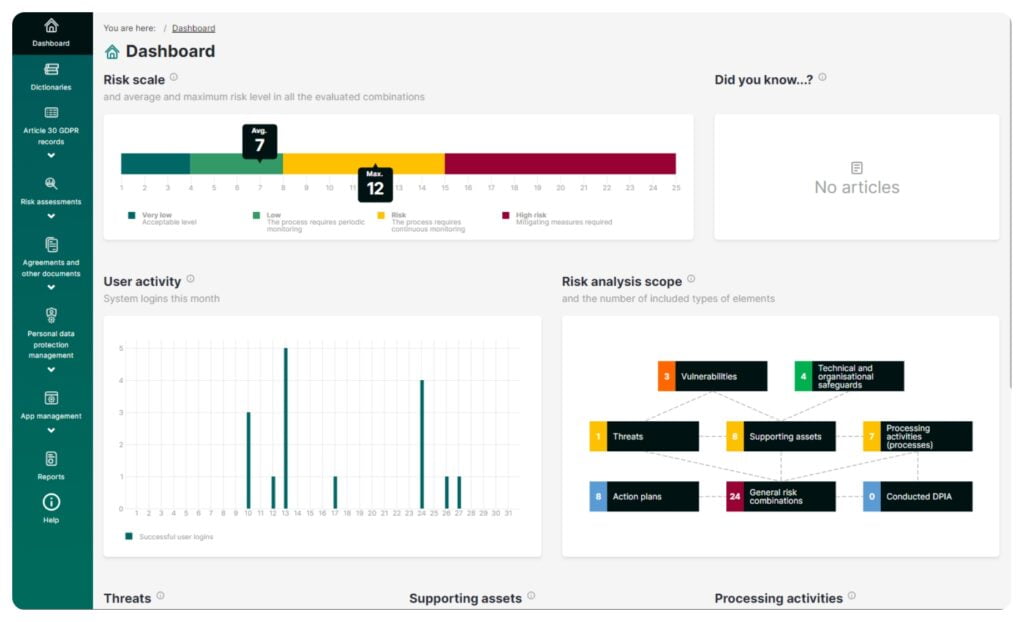
Reports
This feature allows you to:
- Export aggregate lists of data from all the key app functionalities as xlsx files for archiving or audit purposes
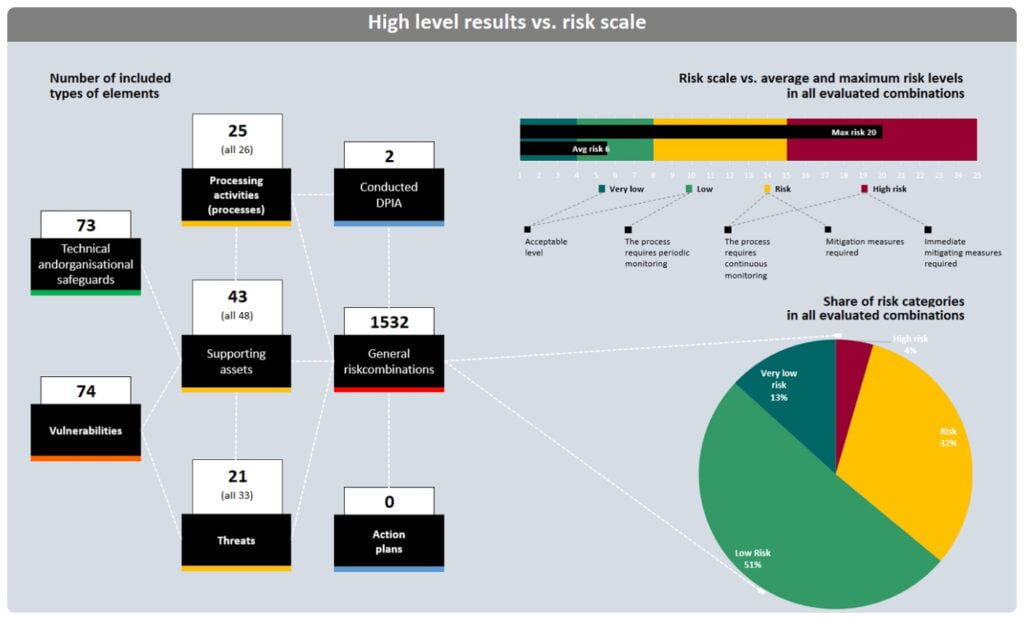
- Prepare clear and transparent reports which give you insight into processes, resources and threats that pose the biggest risk to data security across an organization. The reports are helpful in drawing up effective procedures
- Compile reports which support an analytical approach to the processess occurring across the organization. The reports will enable you to find and evaluate threats and to make appropriate changes in management operations
- Generate reports in a clear and readable format, ready to be printed or presented to your organization’s executive team as a so-called heat map
- Get extended reports including analytical threat maps which enable further (drill-down) detailed analysis
- Generate a report on risk distribution across the organization with a breakdown of organizational units
- Get a quick overview of the risks according to any criteria thanks to movable tables (for example, you can check which processing activities would be affected by the company server malfunction)
Extensive help system
An extensive collection of more than 300 articles including manuals for each of the modules, which not only describe how particular functionalities work but also explain the methods used and serve as a valuable source of knowledge about the principles of personal data protection. The help section is a comprehensive know-how platform made available to the app users by DAPR sp. z o.o. Dedicated articles take the user step by step through the functionalities and their legal grounds, which is key from the perspective of ensuring accountability.
Moduł “Cyber”

Process register
We have created a process register connecting with RCP, but for the purpose of the CYBER analysis, taking into account information assets that comply with standards.
Organization mapping system
A new business object mapping functionality which facilitates clear mapping of related elements and mutual relationships has been introduced:
- Supporting assets, security and vulnerabilityReply 1Anna PrzybyłGuest3 hours ago
- Threats and supporting assets
- Threats, security and vulnerabilities


Automated risk assessment for information security
We have introduced automation of probability ratings and automation of Information Security Impact Assessment based on:
- Assignment of information assets of a given stakeholder to a supporting asset
- The maximum value of the information assets of a given stakeholder
Automated risk assessment for business continuity
We have introduced probability assessment automation and impact assessment for business continuity automation based on:Reply 1Anna PrzybyłGuest3 hours ago
- Mapped relevance of the process to the product
- Relevance of the supporting asset for the process


Threat analytics
We have prepared a new risk analytics module which allows you to create and view risk maps, including
- Dynamic filtering
- Possibility to add and manipulate the order of columns and rows (drag&drop)
- Dynamic aggregation
- Building one-, two- or multidimensional analytical perspectives
- Changing the way of summarizing from counting items, summing values and calculating the percentage share
Management of risk management plans
A new module of action plans has been implemented, which enables modeling of plans:
- On a flexible level: threats, assets, vulnerabilities
- For selected or all domains (GDPR, CYBER)
- With different ways of impact- reduction of the probability of materialization of the threat, reduction of consequences, reduction of the likelihood of consequences
- With the option to enable or disable the plan and to view its operation in the analytics module


Reports
New possibilities of preparing reports according to the user’s needs
Do you want to grow your business?
Start for free | No credit card required